How Easy is It to Get Virus From Torrenting
Computer viruses can spread in many different ways, including via torrent files. In fact, many popular torrent sites are absolutely littered with malware.
In the past, if you were careful about what you clicked or downloaded you could avoid getting infected. But today, even the simple act of viewing a malicious advertisement can result in a full-blown computer virus infection. Because torrent website rarely screen their advertisers, "malvertisement" virus attacks are becoming increasingly common.
Fortunately, there are simple yet effective countermeasures you can deploy to protect your computer and keep it safe from attack. Read on to learn more about the most dangerous computer viruses and find out what you can do to protect yourself against infected torrents.
[toc]
Computer viruses in a nutshell
The term "computer virus" is the umbrella phrase that's used to describe any type of unwanted program that harms your system.
In many ways, computer viruses resemble human viruses. There are many different types of computer viruses, and each type uses a different set of tactics to infiltrate your system.
Aggressive vs. stealthy viruses
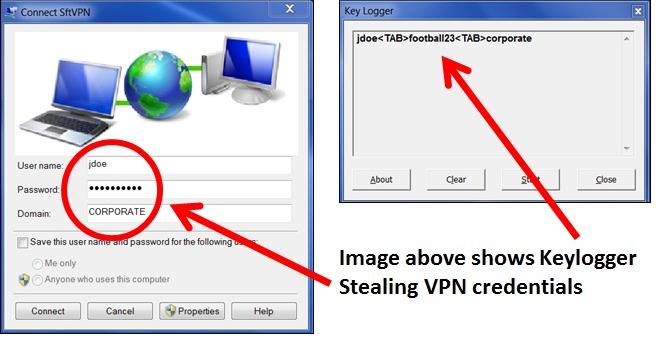
Just because your computer seems healthy doesn't mean that it isn't infected. Some computer viruses are obvious, but others are sneaky. For example, "keylogger" viruses remain hidden and run in the background as you type. They record your usernames and passwords and periodically send your data to a server.
Other aggressive types of viruses– like the WannaCry virus that infected over a quarter of a million computers in May of 2017— are designed to lock users out of their computers and collect money in the form of "ransom" fees.
Here are the 2 major ways that a virus can get onto your system while you torrent.
Transmission method #1: Malvertisements
Malvertisements are banner ads and other types of advertisements that spread and distribute virus files. In certain cases simply looking at a malvertisement is sometimes all you have to do to catch a virus from it (keep reading for details).
Technically, any website can carry a malvertisement. Malvertisements have been identified on Google Ads and other reputable ad programs. But because torrent sites usually don't screen their advertisers very well, you are much more likely to encounter a malvertisement while visiting a torrent site.
The Pirate Bay malvertisements

In May of 2016, security experts identified a malvertisement on The Pirate Bay. The malicious advertiser that posted the ad was using the popular torrent site to transmit "exploit kits" to its visitors.
- Tip: An exploit kit is software that automatically identifies weak spots. Hackers use data gleaned from exploit kits to attack internet users.
After the hackers used the exploit kit to identify computers that were vulnerable, they then infected them with the Cerber "ransomware" virus. The Cerber virus is similar to the WannaCry virus that recently made headlines for locking down thousands of computers all over the world.
The Cerber ransomware virus is reeling in big profits for its creators. The developers behind Cerber have created a multi-million dollar affiliate program. Anyone willing to pay the Cerber developers a portion of the money they make from ransoms can use it on any website on the internet.
One of the most dangerous things about malvertisements is the fact that you often don't even have to click anything to get the virus.
"The interesting thing about infections delivered through malvertising is that it does not require any user action (like clicking) to compromise the system and it does not exploit any vulnerabilities on the website or the server it is hosted from." – Symantec official blog
Malvertisements are becoming increasingly popular because they provide an easy way for hackers to quickly infect millions of website visitors. According to ZDNet, malvertisements infect 12 million computers every month.
Transmission method #2: Downloads
Infected downloads are another serious threat that you should be aware of when you download torrent files.
Hackers often use popular software to transmit viruses. They embed the infected code into the software's installer. Then, when you install the infected program the virus gets copied to your system.
Hackers often use "crackers" or "KeyGens" to break a piece of software's copyright protection system. Sometimes, these tools are simply there to help downloaders crack unlicensed software. However, these same tools can often be viruses in disguise.
Identifying sketchy torrents
Here are a few simple steps you can take to avoid downloading infected torrent files.
Step #1: Check the release group
When torrents first became popular in the early 2000s, it was very hard to know what you were getting before you downloaded it. But over the years, torrent uploaders have organized into tightly-knit associations.
Today's most popular torrents are released by highly systematic warez groups. Warez groups compete with each other to see who can put out the best content. They even attach brand names to their releases. For example, you may run across releases from the well-known warez group known as YIFY if you search for movies on Pirate Bay.
Step #2: Check the format
In addition to recognizable brand names, content that is released as official warez follows a detailed set of standards, including uniform file name conventions. Content that contains malware or does not follow warez standards gets "nuked"— or in other words, labeled as bad and taken out of circulation.
Step #3: Check the comments section
Comments can provide a clue about the quality of a file. If the comments are left by real users, they can be helpful in sorting out the good torrents from the bad. However, beware of fake comments left by "sockpuppet" accounts. Sockpuppet accounts are fake online identities used by hackers to entice downloaders into downloading viruses.

Usually it's easy to spot praise left by a sockpuppet account. Most torrent sites award badges to trusted contributors. For example, trusted Pirate Bay commentators have green, pink or blue skulls next to their user names.
Step #4: Stick to well known torrent sites
Before you download a torrent from a site, look at it closely. There are many copycat torrent sites out there that are not what they seem to be. Check the site's URL to make sure that it is legit before you proceed. Certain viruses are capable of hijacking random websites in order to create pages of files that seem to be torrents, but are in fact malware.
Step #5: Avoid unpopular torrents
Just because a torrent isn't popular doesn't mean that it's unsafe. But if hundreds of people are participating in the torrent swarm, the odds are definitely in your favor. Torrents that contain malware tend to get weeded out pretty fast by moderators. For example, Pirate Bay relies on about a dozen or so experienced moderators.
Virus protection fundamentals
If you have a good anti-virus program and download security patches as soon as they come out, you'll have a better chance of staying safe from viruses.
Tip #1: Install anti-virus software
The best way to defend against viruses when you torrent is by using anti-virus software. Anti-virus software runs in the background when you use your computer, scanning every file you open. There are several great anti-virus programs that are completely free, so there is really no excuse to not install one.
If your anti-virus program detects a virus, it will quarantine and remove any malicious code it finds. Good anti-virus programs can also perform periodic deep scans, which are useful for detecting any dormant viruses or viruses that may have somehow slipped through the cracks.
Free anti-virus software suites
According to PCMag, Avast and AVG are the two best free anti-virus programs out there right now. Both programs can identify viruses "heuristically," by using behavioral data to spot code that seems as though it may have been designed to damage or hijack your computer. Additionally, both Avast and AVG can run both real-time and on-demand virus scans.
The best premium anti-malware software suite for torrenters
We think Malwarebytes is a great security choice for torrenters because it's specifically designed to block the kinds of attacks that torrenters encounter. Malwarebytes employs four independent modules (anti-malware, anti-ransomware, anti-exploit, and malicious website protection) to block and remove malicious code. Malwarebytes is not free, but it is fairly cheap and you can try it out for 14 days before you hit the paywall.
False alarms
Some legitimate tools that come with torrent files will set off false alarms when you try to use them. However, common sense will often reveal whether or not the tool you downloaded contains a virus. If the torrent is popular and has good reviews from trusted accounts, odds are high that the tool is legitimate.
If you still aren't sure that you can trust the tool you downloaded, try reaching out to the developer of the tool for confirmation. Many developers that create torrenting tools are surprisingly easy to reach. Additionally, there is a free online tool called VirusTotal that you can use to scan suspicious files and websites. VirusTotal can compare a file against 40 different virus databases. If the file only triggers one database, odds are high that it's just a false positive.
Tip #2: Keep all your software up-to-date
Unfortunately, most software programs and operating systems are designed with functionality in mind– not security. Most security bugs don't cause any obvious problems. Yet, hackers can exploit them and use them to gain access to your computer.
One good example of how hackers can use software bugs to gain control of consumer computers is the hacking tool known as EternalBlue. EternalBlue was originally developed by the NSA, but the hacker group called the Shadow Brokers released it to the general public in April of 2017. As a result, now every hacker on the planet can use it.
EternalBlue takes advantage of a bug in the Windows networking protocol known as SMB (Server Message Block). People around the world use SMB-based Windows networks every day to do ordinary things like print out documents and share files.
If you have an old version of SMB, a hacker can use EternalBlue to take over your computer. But if you have downloaded the latest Windows security updates for SMB, your computer will be protected from EternalBlue.
Up-to-date computers are hard to hack
Security experts work diligently to find and fix security bugs before hackers can identify them and take advantage. According to the makers of Symantec Norton, ordinary software updates are actually very effective at stopping computer viruses.
"It's perhaps a sweet irony that the very medium used for virus proliferation and other threats is also a delivery mechanism for anti-threat technology. But the reality is security firms can use the Internet just as effectively as hackers." – Symantec norton blog
The makers of popular software programs like Windows and Google Chrome also work around the clock to make life harder for hackers. So, be sure to download new security patches as soon as you possibly can after they come out.
Windows security patches
On Windows, you can use Windows Update to get the latest security patches automatically. Alternatively, you can download the patches manually via the official Windows website.
MacOS security patches
If you have a Mac, you can use Apple's Mac Store program to download daily security updates. Like Microsoft, Apple also has a convenient list of download links for security updates on its official site.
Notable computer viruses
The viruses listed below have been making headlines lately. Here's a quick overview of how these infamous viruses work and what you can do if your computer gets infected with them.
Cerber

The Cerber virus is a ransomware virus. It encrypts your files, and then provides a Tor Browser ransom payment link.
- Tip: The Tor Browser allows access to the "Deep Web," which is a totally anonymous part of the internet that's often frequented by drug dealers and other criminals.
If your computer gets infected with Cerber, all the files on your computer will get locked inside of container files labeled with the .cerber extension.
Typical Cerber ransom fees start at around 1 bitcoin. However, the amount goes up the longer you wait. Unfortunately, many people who pay the ransom never receive the link that allows them to unlock their files.
What to do if you get the Cerber virus
Removing the Cerber virus itself is easy. Kaspersky, Symantec, AVG or any other major anti-virus software suite can get rid of it. The hard part is decrypting the encrypted Cerber files that the virus leaves behind.
Paying the ransom is not a good idea because the money encourages the hackers, and there's no guarantee that paying up will actually decrypt your files. A better alternative to forking over bitcoin and hoping for the best is the No More Ransom website. The No More Ransom project is a coalition of law enforcement and IT security experts that work together to create free anti-ransomware tools.
WannaCry

The WannaCry virus has the same modus operandi as Cerber: it locks down computers and encrypts all of their files.
Fortunately, an anonymous 22-year-old researcher from the UK has found a "kill switch" for WannaCry. He discovered that whoever created the WannaCry designed it to turn off in the event that it could reach a nonexistent website with a nonsensical name. After finding the name of the website in WannaCry's code, he registered the site and turned it on. WannaCry attacks stopped immediately.
WannaCry isn't over yet
A version of WannaCry that lacks the "kill switch" weakness mentioned above is still floating around on the web: UiWix. UiWix exploits the same Windows weakness that WannaCry took advantage of, only it's sneakier and harder to disable. Additionally, the anonymous researcher that stopped WannaCry has said that attacks against the website used to disable the virus could potentially bring WannaCry back to life.
What to do if you get the WannaCry/UiWix virus
Like Cerber, the problem with WannaCry/UiWix is not removing the virus itself. Any good anti-virus software suite can get rid of it. The difficulty with it lies in decrypting the actual files that the virus affects.
Fortunately, there's a quick fix for WannaCry victims running Windows XP to Windows 7: WannaKiwi. WannaKiwi is a tool that uses prime numbers to break WannaCry's encryption. to learn more about WannaKiwi, read this article from "white hat" hacker Matt Suiche.
Sathurbot
Sathurbot is subtle compared to WannaCry and Cerber. Instead of locking down individual computers and forcing their users to pay ransoms, Sathurbot allows you to continue using your computer normally. But in the background, it runs a program that attempts to break into WordPress websites.
The Sathurbot virus uses torrent networks to replicate itself, so if you like to download torrents you may be at risk. Sathurbot is especially dangerous because it allows hackers to install additional viruses on your device.
What to do if you get the Sathurbot virus
Fortunately, the major anti-virus software makers have already caught on to the Sathurbot virus. All you need to do is run your anti-virus program and follow its instructions to remove it from your computer.
Summary
With so many dangerous viruses floating around on the web, it's more important than ever before to pay attention to internet security fundamentals. If you use an anti-virus program to protect yourself while you torrent and keep all your software up-to-date, you'll most likely be able to avoid getting infected. But if you put off the updates for another day and neglect to use an anti-virus program when you download torrents, you're giving hackers the opportunity to take advantage of your vulnerabilities.
Alex Munkachy
Alex Munkachy is a freelance writer, game developer and hobby robotics enthusiast. You can find his blog about robotics news and reviews at robotfanatics.com.
Source: https://flixed.io/virus-downloading-torrents/
0 Response to "How Easy is It to Get Virus From Torrenting"
Enregistrer un commentaire